Get valid 70-686 PDF dumps or VCE dumps from PassLeader, we guarantee our 200q 70-686 exam questions are the newest and all the new 70-686 exam questions and answers are available. Now try our best 70-686 practice test with VCE dumps or PDF dumps and you will acquire Pro: Windows 7, Enterprise Desktop Administrator certification immediately.
keywords: 70-686 exam,200q 70-686 exam dumps,200q 70-686 exam questions,70-686 pdf dumps,70-686 vce dumps,70-686 braindumps,70-686 practice test,70-686 study guide,Pro: Windows 7, Enterprise Desktop Administrator Exam
QUESTION 71
A company uses Microsoft Deployment Toolkit (MDT) 2010 to deploy Windows 7 Enterprise and Microsoft Office 2010. The company is replacing existing computers with new 64-bit computers. You have the following requirements:
* You need to include Office 2010 with the deployment.
* You need to automate the deployment where possible.
* Some employees have accessibility requirements that require specialized hardware.
* The hardware must continue to be used after the deployment.
* The specialized hardware is compatible with Windows 7 but only 32-bit drivers are available from the manufacturer.
You need to create an image that meets these requirements. What should you do? (Choose all that apply.)
A. Import the Windows 7 Enterprise x86 source files.
B. From the MDT deployment workbench, select the Custom Task Sequence template.
C. Use a reference computer and capture a WIM image.
D. From the MDT deployment workbench, select the Sysprep and Capture template.
E. Import the necessary OEM drivers
F. Import the 32-bit version of Office 2010.
G. Import the 64-bit version of Office 2010.
H. Import the Windows 7 Enterprise x64 source files.
QUESTION 72
Your company’s network includes a main office and several branch offices. The branch offices are connected to the main office by high-latency links. All client computers run Windows 7 Enterprise, and all servers run Windows Server 2008 R2. Servers are located in each of the branch offices. Client computers in the branch offices frequently access a specific group of files on a file server named Server1. These access requests consume significant amounts of bandwidth and reduce the speed of higher-priority traffic. You need to reduce the bandwidth that is consumed by requests for frequently accessed files. What should you do?
A. Configure BranchCache in Hosted Cache mode on client computers in the main office and the branch offices.
B. Configure BranchCache in Distributed Cache mode on client computers in the main office and the branch offices.
C. Enable the BranchCache For Network Files role service on Server1. Configure BranchCache in Distributed Cache mode on a server computer in only the branch offices.
D. Enable the BranchCache For Network Files role service on Server1. Configure BranchCache in Hosted Cache mode on a server computer in only the branch offices.
Answer: D
QUESTION 73
A Windows Server 2008 R2 server named SERVER01 has the Windows Deployment Services (WDS) role installed. SERVER02 is running DHCP services. You prestage computer objects in Active Directory. You plan to use WDS to deploy Windows 7 to the prestaged computers. When you try to deploy an image by using PXE, the process fails. You need to ensure that SERVER01 responds to prestaged client computers only. From WDS, what should you do? (Choose all that apply.)
A. On the DHCP tab, select Configure DHCP option 60 to indicate that this server is also a PXE server.
B. On the Advanced tab, select Authorize this Windows Deployment Services server in DHCP.
C. On the PXE Response tab, select Respond to all client computers (known and unknown).
D. On the DHCP tab, select Do not listen on Port 67.
E. On the PXE Response tab, select Respond only to known client computers.
F. On the Advanced tab, select Do not authorize this Windows Deployment Services server in DHCP.
Answer: BE
QUESTION 74
You are preparing to install a 32-bit legacy application on all client computers in an organization. The application requires specific compatibility settings in order to function in Windows 7. You run the 32-bit version of Compatibility Administrator and create a new application fix. You need to create a shim database that includes a compatibility fix for applications that have known issues with the Desktop Window Manager. Which compatibility modes should you select? To answer, select the appropriate setting in the work area.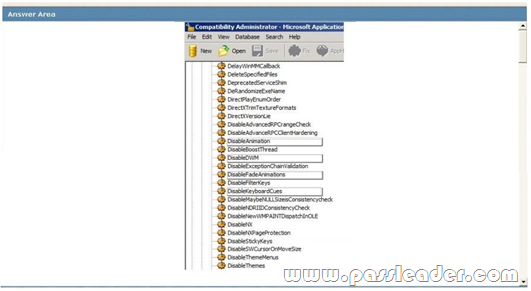
Answer: 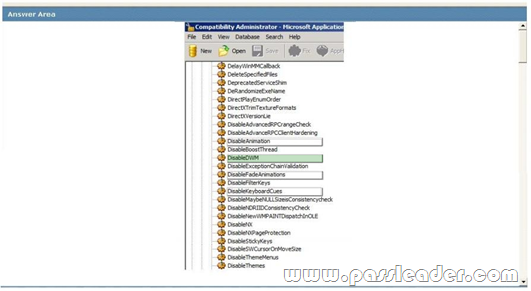
QUESTION 75
Your company has a custom Web application that uses a self-signed SSL certificate. The company has an internal certification authority (CA) and uses autoenrollment. When external users attempt to start the Web application, Internet Explorer displays an error message that recommends closing the Web page rather than continuing to the application. You need to ensure that Internet Explorer does not display the error message. What should you do?
A. Install the current certificate into the personal store on each client computer. Add the applications URL to the Trusted Sites zone in Internet Explorer.
B. Install the current certificate into the computer store on each client computer.
C. Purchase and install a commercial certificate on the CA server. Ensure that users trust the issuing CA.
D. Issue a root certificate from the internal CA on the external users computers.
Answer: B
QUESTION 76
Your companys network is shown in the following diagram.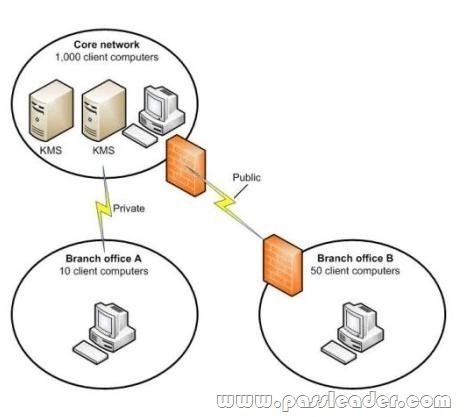
There is a VPN between Branch Officebranch office B and the Core Networkcore network. The company plans to deploy Windows 7 to all client computers. You need to manage the deployment to ensure that client computers in branch office A and in branch office B can activate Windows. What should you do? (Each correct answer presents part of the solution. Choose all that apply.)
A. Configure DNS so that client computers in branch office A use the Key Management Service (KMS) in the core network.
B. Deploy the Key Management Service (KMS) in branch office B.
C. Deploy the Key Management Service (KMS) in branch office A.
D. Configure DNS so that client computers in branch office B use the Key Management Service (KMS) in the core network.
Answer: AB
QUESTION 77
Your company has an Active Directory Domain Services (AD DS) forest with a single domain named contoso.com. You deploy a new Group Policy object (GPO) named California Computers GPO as part of the organizational unit (OU) and GPO design shown in the following diagram.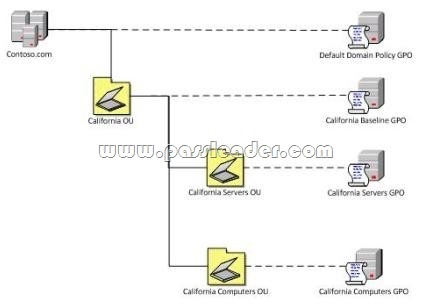
The California Computers GPO contains computer configuration settings and user configuration settings. User configuration settings are not being applied to users who log on to client computers in the California Computers OU. Which GPO setting should you select?? (To answer, drag the appropriate setting from the list of settings to the correct location or locations in the work area.)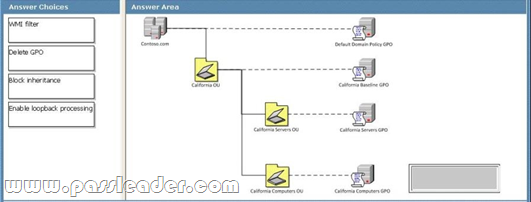
Answer: 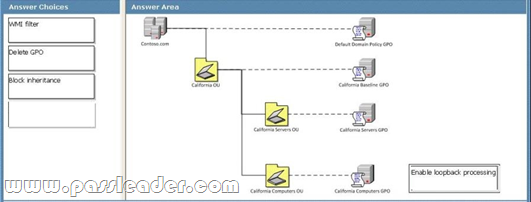
QUESTION 78
You are deploying an App-V client application to the New York office. You need to ensure that the application will be installed at a specific time. What should you use to deploy the application?
A. ConfigMgr
B. a Group Policy object (GPO) with a software installation policy.
C. MED-V
D. Microsoft Deployment Toolkit
Answer: A
QUESTION 79
Your company has client computers that run Windows 7 Enterprise. Each computer in the company is required to boot into a different Windows 7 application environment without compromising the main Windows 7 Enterprise installation. You need to create a new Native Boot VHD that will host the alternate Windows 7 environments. Which command should you use?
A. BCDEdit.exe
B. Bootcfg.exe
C. DiskPart.exe
D. BCDboot.exe
Answer: C
QUESTION 80
Your company has a single Active Directory Domain Services (AD DS) domain and 1,000 Windows 7 computers. You are planning to deploy a custom application. You need to schedule the deployment to occur outside of business hours and without user interaction. What should you do? (Choose all that apply.)
A. Create a collection with the required computers and assign the software to the collection.
B. Create a software installation Group Policy object (GPO).
C. Assign the policy to the root of the Active Directory Domain Services (AD DS) domain.
D. Create a software deployment package by using System Center Configuration Manager 2007.
E. Create an unattend.xml file.
F. Create a silent install MSI file.
Answer: ADF
http://www.passleader.com/70-686.html
QUESTION 81
A network consists of 1,000 laptop computers that run Windows XP. The computers do not have access to the corporate network. You plan to migrate 200 of the computers immediately to Windows 7. The remainder will be migrated over the next several months. You need to plan the most efficient method for activating all of the computers. What should you do?
A. Use Multiple Activation Key (MAK) Independent for the first 200 computers, and then use Multiple Activation Key (MAK) Proxy for the remaining computers.
B. Use the Key Management Service (KMS) for all the computers.
C. Use Multiple Activation Key (MAK) Independent for all the computers.
D. Use Multiple Activation Key (MAK) Proxy for the first 200 computers, and then use the Key Management Service (KMS) for the remaining computers.
Answer: B
QUESTION 82
Your company’s network is shown in the following diagram.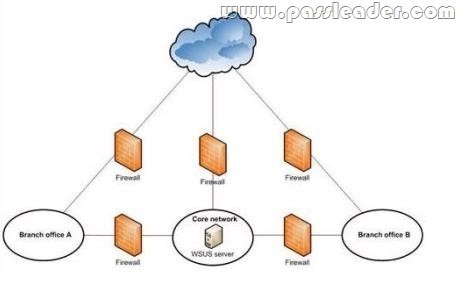
Each office is connected to the Internet through a high-bandwidth connection. The branch offices are connected to the core network through low-bandwidth connections. Microsoft Windows Server Update Services (WSUS) must provide software updates for all offices. You need to design the WSUS infrastructure to minimize traffic over the low-bandwidth connections. Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
A. Deploy BranchCache on the WSUS server and client computers
B. Configure WSUS to use updates that are stored locally
C. Configure WSUS to use updates that are stored on Microsoft Update
D. Deploy Quality of Service (QoS) on the WSUS server and client computers
E. Deploy WSUS servers in the branch offices
Answer: CE
QUESTION 83
Your network is configured as shown in the following diagram.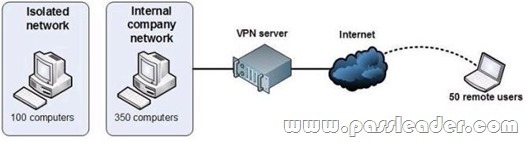
You are planning to deploy Windows 7. You have the following requirements:
* Use BitLocker on all computers in the isolated network.
* Provide DirectAccess on all portable computers.
* Use the Key Management Service (KMS) to activate all client computers.
You need to plan a client computer licensing strategy that meets the requirements. What should you do?
A. License 500 copies of Windows 7 Ultimate.
B. License 500 copies of Windows 7 Enterprise.
C. License 350 copies of Windows 7 Professional, license 150 copies of Windows 7 Ultimate, and purchase Software Assurance for the Windows 7 Professional licenses.
D. License 350 copies of Windows 7 Enterprise, and license 150 copies of Windows 7 Ultimate.
Answer: B
QUESTION 84
Your company has 1,000 client computers that run Windows 7. The company uses several custom line-of-business applications that are not compatible with Windows 7. You need to distribute a Microsoft Enterprise Desktop Virtualization (MED-V) virtual machine (VM) image that includes the custom applications to all Windows 7 client computers. What should you do?
A. Mount the VM image from the MED-V workspace.
B. Deploy the VM image from the MED-V server.
C. Deploy the VM image by using Windows Deployment Services (WDS).
D. Deploy the VM image by using Windows Server Update Services (WSUS).
Answer: B
QUESTION 85
Your company plans to upgrade all client computers to Windows 7. The company uses a custom line-of-business application. The application contains sensitive data. The application will not run on Windows 7. You establish that Microsoft Enterprise Desktop Virtualization (MED-V) is the appropriate technology to allow your organization to continue to use the application. You need to ensure that the virtual machine (VM) images that contain sensitive data can be used only when the user is connected to the MED-V server. What should you do?
A. Using MED-V TrimTransfer technology, deploy the VM image over the network
B. In the MED-V console, configure the MED-V workspace to prevent offline operation
C. Use BitLocker Drive Encryption to encrypt the drive on which the VM image is stored
D. Using Microsoft System Center Configuration Manager, deploy the VM image to an image store directory
Answer: B
QUESTION 86
The client computers in your network run either Windows XP or Windows 7. All client computers are in a single Active Directory Domain Services (AD DS) organizational unit (OU) named MyClients. You install Windows Software Update Services (WSUS). You create a Group Policy object (GPO) that enables automatic updates from the WSUS server, and you link the GPO to the MyClients OU. You place all client computers in a targeting group named MyClients. Testing reveals that a security update that is applicable to both Windows XP and Windows 7 causes a line-of-business application to fail on the Windows XP client computers. You need to ensure that the application runs on the Windows XP client computers and that the Windows 7 client computers receive the security update. What should you do?
A. Remove the Windows XP client computers from the MyClients targeting group. Approve the update for installation to the All Computers targeting group.
B. Remove the Windows 7 client computers from the MyClients targeting group. Approve the update for installation to the All Computers targeting group.
C. Create a targeting group named MyXPClients beneath the MyClients targeting group. Move the Windows XP client computers to the MyXpClients targeting group. Approve the update for installation to the MyClients targeting group.
D. Remove the Windows 7 client computers from the MyClients targeting group. Approve the update for installation to the Unassigned Computers targeting group.
Answer: D
QUESTION 87
You are planning to upgrade Microsoft Internet Explorer. You must create a report that identifies which computers are successfully upgraded. You need to design a deployment method that meets this requirement. What should you use? (Choose all that apply.)
A. Microsoft System Center Essentials
B. Windows Intune
C. Microsoft System Center Configuration Manager
D. Internet Explorer Administration Kit (IEAK) and Group Policy
E. Windows Server Update Services (WSUS)
Answer: ABDE
QUESTION 88
Your network has a single domain with 1,000 client computers that run Windows 7. You use Microsoft System Center Configuration Manager 2007 to distribute and install software applications. All users have standard user accounts. You plan to use Group Policy to ensure that application installation functions properly. You need to design the User Account Control (UAC) policy. Which setting should you select? To answer, select the appropriate setting in the work area.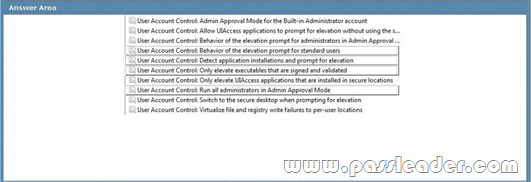
Answer: 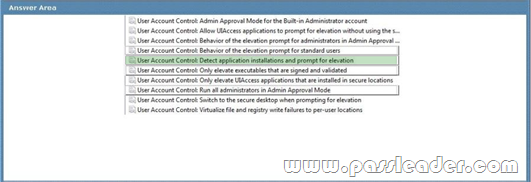
QUESTION 89
You are creating a Windows 7 image. You need to prevent users from sharing their desktop sessions with remote users. You also need to allow administrators who are using Windows XP to administer the Windows 7 image remotely. Which settings should you configure? To answer, select the appropriate setting or settings in the work area.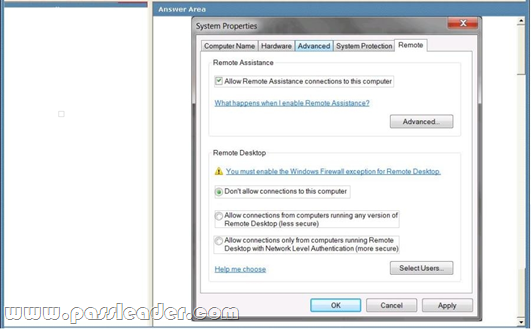
Answer: 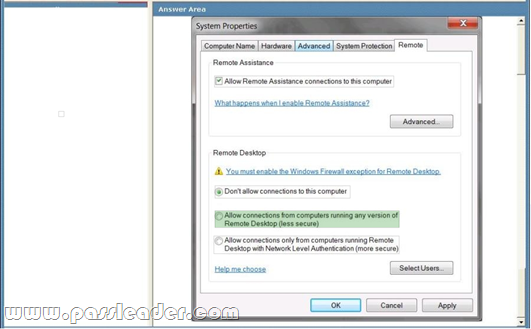
QUESTION 90
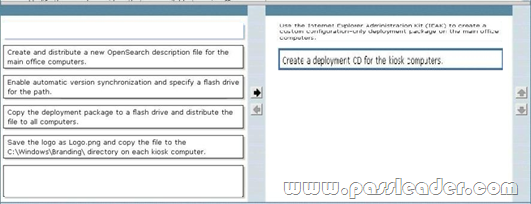
A company has 1,000 computers in the main office and 20 computers in store kiosks. All the computers run Windows 7 Enterprise. The kiosk computers do not have network connections. The company brands the Microsoft Internet Explorer program window on all computers by displaying the company logo at the left end of the title bar. The company changes its logo. You have the following requirements:
* Display the new logo on the Internet Explorer program window title bar on the main office computers and the kiosk computers.
* Modify the search providers that are available to main office computers.
You need to define Internet Explorer settings to support the requirements. Which two actions should you perform in sequence?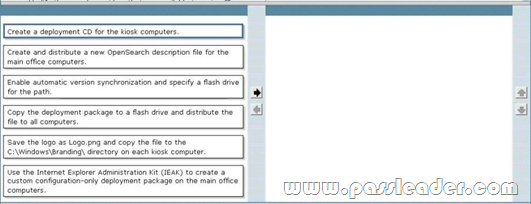
Answer: