How to pass the newest 70-640 exam? What new questions are on the latest 70-640 exam? PassLeader’s best 70-640 VCE and PDF exam dumps/70-640 sample questions will tell you all about the 70-640 exam. For all PassLeader’s 651q 70-640 exam questions are the newest and covered all new added questions and answers, which will help you 100% passing exam. And we PassLeader will continue update 70-640 exam questions and answers, you will never fail the 70-640 exam. Hurry up and get the free VCE Player with your premium 70-640 VCE dumps from passleader.com now!
keywords: 70-640 exam,651q 70-640 exam dumps,651q 70-640 exam questions,70-640 pdf dumps,70-640 practice test,70-640 vce dumps,70-640 study guide,70-640 braindumps,TS: Windows Server 2008 Active Directory, Configuring Exam
QUESTION 321
Your network contains an Active Directory forest. The forest contains multiple domains. You need to ensure that users in the human resources department can search for employees by using the employeeNumber attribute. What should you do?
A. From Active Directory Sites and Services, modify the properties of each global catalog server.
B. From the Active Directory Schema snap-in, modify the properties of the user object class.
C. From Active Directory Sites and Services, modify the NTDS Settings objectof each global catalog server.
D. From the Active Directory Schema snap-in, modify the properties of the employeeNumber attribute.
QUESTION 322
Your network contains a single Active Directory domain. The domain contains an enterprise certification authority (CA). You need to ensure that the encryption keys for e-mail certificates can be recovered from the CA database. You modify the e-mail certificate template to support key archival. What should you do next?
A. Issue the key recovery agent certificate template.
B. Run certutil.exe -recoverkey.
C. Run certreq.exe-policy.
D. Modify the location of the Authority Information Access (AIA) distribution point.
Answer: A
QUESTION 323
Your network contains an Active Directory-integrated DNS zone named contoso.com. You discover that the zone includes DNS records for computers that were removed from the network. You need to ensure that the DNS records are deleted automatically from the zone. What should you do?
A. From DNS Manager, set the aging properties.
B. Create a scheduled task that runs dnslint.exe /v /d contoso.com.
C. From DNS Manager, modify the refresh interval of the start of authority (SOA) record.
D. Create a scheduled task that runs ipconfig.exe /flushdns.
Answer: A
QUESTION 324
Your network contains a domain controller that runs Windows Server 2008 R2. You run the following command on the domain controller:
dsamain.exe C dbpath c:\$SNAP_201006170326_VOLUMEC$\Windows\NTDS\ntds.dit C ldapport 389 – allowNonAdminAccess
The command fails. You need to ensure that the command completes successfully. How should you modify the command?
A. Change the value of the -dbpath parameter.
B. Include the path to Dsamain.
C. Change the value of the -ldapport parameter.
D. Remove the CallowNonAdminAccess parameter.
Answer: C
QUESTION 325
Your network contains an Active Directory domain. The domain contains 10 domain controllers that run Windows Server 2008 R2. You need to monitor the following information on the domain controllers during the next five days:
– Memory usage
– Processor usage
– The number of LDAP queries
What should you do?
A. Create a User Defined Data Collector Set (DCS) that uses the Active Directory Diagnostics template.
B. Use the System Performance Data Collector Set (DCS).
C. Create a User Defined Data Collector Set (DCS) that uses the System Performance template.
D. Use the Active Directory Diagnostics Data Collector Set (DCS).
Answer: A
QUESTION 326
Your network contains an Active Directory domain named contoso.com. Contoso.com contains a domain controller named DC1 and a read-only domain controller (RODC) named RODC1. You need to view the most recent user accounts authenticated by RODC1. What should you do first?
A. From Active Directory Sites and Services, right-click the Connection object for DC1, and then click Replicate Now.
B. From Active Directory Sites and Services, right-click the Connection object for DC2, and then click Replicate Now.
C. From Active Directory Users and Computers, right-click contoso.com, click Change DomainController, and then connect to DC1.
D. From Active Directory Users and Computers, right-click contoso.com, click Change Domain Controller, and then connect to RODC1.
Answer: C
QUESTION 327
Your network contains an Active Directory domain. The domain contains 3,000 client computers. All of the client computers run Windows 7. Users log on to their client computers by using standard user accounts. You plan to deploy a new application named App1. The vendor of App1 provides a Setup.exe file to install App1. Setup.exe requires administrative rights to run. You need to deploy App1 to all client computers. The solution must meet the following requirements:
– App1 must automatically detect and replace corrupt application files.
– App1 must be available from the Start menu on each client computer.
What should you do first?
A. Create a logon script that calls Setup.exe for App1.
B. Create a .zap file.
C. Create a startup script that calls Setup.exe for App1.
D. Repackage App1 as a Windows Installer package.
Answer: D
QUESTION 328
Your network contains an Active Directory domain named contoso.com. Contoso.com contains two sites named Site1 and Site2. Site1 contains a domain controller named DC1. In Site1, you install a new domain controller named DC2. You ship DC2 to Site2. You discover that certain users in Site2 authenticate to DC1. You need to ensure that the users in Site2 always attempt to authenticate to DC2 first. What should you do?
A. From Active Directory Users and Computers, modify the Location settings of the DC2 computer object.
B. From Active Directory Sites and Services, modify the Location attribute for Site2.
C. From Active Directory Sites and Services, move the DC2 server object.
D. From Active Directory Users and Computers, move the DC2 computer object.
Answer: C
QUESTION 329
Your network contains an Active Directory domain. The domain contains an enterprise certification authority (CA). You need to ensure that only members of a group named Admin1 can create certificate templates. Which tool should you use to assign permissions to Admin1?
A. the Certification Authority console
B. Active Directory Users and Computers
C. the Certificates snap-in
D. Active Directory Sites and Services
Answer: A
QUESTION 330
Your network contains an Active Directory domain named contoso.com. Contoso.com contains a server named Server2. You open the System properties on Server2 as shown in the exhibit. (Click the Exhibit button.)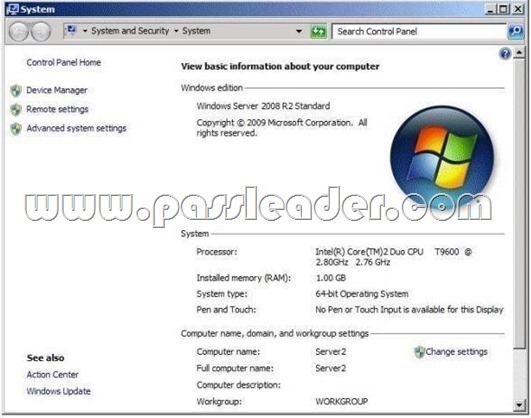
When you attempt to configure Server2 as an enterprise subordinate certification authority (CA), you discover that the enterprise subordinate CA option is unavailable. You need to configure Server2 as an enterprise subordinate CA. What should you do first?
A. Upgrade Server2 to Windows Server 2008 R2 Enterprise.
B. Log in as an administrator and run Server Manager.
C. Import the root CA certificate.
D. Join Server2 to the domain.
Answer: D
http://www.passleader.com/70-640.html
QUESTION 331
Your network contains an Active Directory domain. All DNS servers are domain controllers. You view the properties of the DNS zone as shown in the exhibit. (Click the Exhibit button.)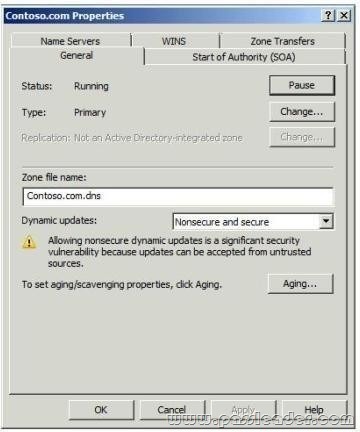
You need to ensure that only domain members can register DNS records in the zone. What should you do first?
A. Modify the zone type.
B. Create a trust anchor.
C. Modify the Advanced properties of the DNS server.
D. Modify the Dynamic updates setting.
Answer: A
QUESTION 332
Your company has a single Active Directory forest with a single domain. Consultants in different departments of the company require access to different network resources. The consultants belong to a global group named TempWorkers. Three file servers are placed in a new organizational unit named SecureServers. The file servers contain confidential data in shared folders. You need to prevent the consultants from accessing the confidential data. What should you do?
A. Create a new Group Policy Object (GPO) and link it to the SecureServers organizational unit. Assign the Deny access to this computer from the network user right to the TempWorkers global group.
B. Create a new Group Policy Object (GPO) and link it to the domain. Assign the Deny access to this computer from the network user right to the TempWorkers global group.
C. On the three file servers, create a share on the root of each hard disk. Configure the Deny Full control permission for the TempWorkers global group on the share.
D. Create a new Group Policy Object (GPO) and link it to the domain. Assign the Deny log on locally user right to the TempWorkers global group.
E. Create a new Group Policy Object (GPO) and link it to the SecureServers organizational unit. Assign the Deny log on locally user right to the TempWorkers global group.
Answer: A
QUESTION 333
Your network contains two Active Directory forests named contoso.com and nwtraders.com. The functional level of both forests is Windows Server 2003. Contoso.com contains one domain. Nwtraders.com contains two domains. You need to ensure that users in contoso.com can access the resources in all domains. The solution must require the minimum number of trusts. Which type of trust should you create?
A. external
B. forest
C. realm
D. shortcut
Answer: B
QUESTION 334
You install an Active Directory domain in a test environment. You need to reset the passwords of all the user accounts in the domain from a domain controller. Which two Windows PowerShell commands should you run? (Each correct answer presents part of the solution, choose two.)
A. $ newPassword = *
B. Import-Module ActiveDirectory
C. Import-Module WebAdministration
D. Get- AdUser -filter * | Set- ADAccountPossword – NewPassword $ newPassword – Reset
E. Set- ADAccountPossword – NewPassword – Reset
F. $ newPassword = (Read-Host – Prompt “New Password” – AsSecureString )
G. Import-Module ServerManager
Answer: DF
QUESTION 335
Your network contains two forests named adatum.com and litwareinc.com. The functional level of all the domains is Windows Server 2003. The functional level of both forests is Windows 2000. You need to create a forest trust between adatum.com and litwareinc.com. What should you do first?
A. Create an external trust.
B. Raise the functional level of both forests.
C. Configure SID filtering.
D. Raise the functional level of all the domains.
Answer: B
QUESTION 336
Your network contains an Active Directory forest named adatum.com. All client computers used by the marketing department are in an organizational unit (OU) named Marketing Computers. All user accounts for the marketing department are in an OU named Marketing Users. You purchase a new application. You need to ensure that every user in the domain who logs on to a marketing department computer can use the application. The application must only be available from the marketing department computers. What should you do?
A. Create and link a Group Policy object (GPO) to the Marketing Users OU. Copy the installation package to a shared folder on the network. Assign the application.
B. Create and link a Group Policy object (GPO) to the Marketing Computers OU. Copy the installation package to a shared folder on the network. Assign the application.
C. Create and link a Group Policy object (GPO) to the Marketing Computers OU. Copy the installation package to a local drive on each marketing department computer. Publish the application.
D. Create and link a Group Policy object (GPO) to the Marketing Users OU. Copy the installation package to a folder on each marketing department computer. Publish the application.
Answer: B
QUESTION 337
Your network contains an Active Directory forest named adatum.com. You need to create an Active Directory Rights Management Services (AD RMS) licensing-only cluster. What should you install before you create the AD RMS root cluster?
A. The Failover Cluster feature
B. The Active Directory Certificate Services (AD CS) role
C. Microsoft Exchange Server 2010
D. Microsoft SharePoint Server 2010
E. Microsoft SQL Server 2008
Answer: E
QUESTION 338
Your network contains an Active Directory domain named contoso.com. The contoso.com domain contains a domain controller named DC1. You create an Active Directory-integrated GlobalNames zone. You add an alias (CNAME) resource record named Server1 to the zone. The target host of the record is server2.contoso.com. When you ping Server1, you discover that the name fails to resolve. You are able to successfully ping server2.contoso.com. You need to ensure that you can resolve names by using the GlobalNames zone. Which command should you run?
A. Dnscmd DCl.contoso.com /ZoneAdd GlobalNames /DsPrimary /DP /domain
B. Dnscmd DCl.contoso.com /config /Enableglobalnamessupport forest
C. DnscmdDCl.contoso.com/config/Enableglobalnamessupport 1
D. Dnscmd DCl.contoso.com /ZoneAdd GlobalNames /DsPrimary /DP /forest
Answer: C
QUESTION 339
Your network contains an Active Directory domain named contoso.com. The network has a branch office site that contains a read-only domain controller (RODC) named R0DC1. R0DC1 runs Windows Server 2008 R2. A user logs on to a computer in the branch office site. You discover that the user’s password is not stored on R0DC1. You need to ensure that the user’s password is stored on RODC1 when he logs on to a branch office site computer. What should you do?
A. Modify the RODC s password replication policy by removing the entry for the Allowed RODC Password Replication Group.
B. Modify the RODC’s password replication policy by adding R0DC1’s computer account to the list of allowed users, groups, and computers.
C. Add the user’s user account to the built-in Allowed RODC Password Replication Group on R0DC1.
D. Add R0DC1’s computer account to the built-in Allowed RODC Password Replication Group on R0DC1.
Answer: C
QUESTION 340
You deploy an Active Directory Federation Services (AD FS) Federation Service Proxy on a server named Server1. You need to configure the Windows Firewall on Server1 to allow external users to authenticate by using AD FS. Which protocol should you allow on Server1?
A. Kerberos
B. SSL
C. SMB
D. RPC
Answer: B
