How To 100% Pass New 70-680 Exam: PassLeader have been launched the newest 580q 70-680 exam dumps with all the new updated exam questions. We provide the latest full version of 70-680 PDF and VCE dumps with new real questions and answers to ensure your 70-680 exam 100% pass, and you will get the free new version VCE Player along with your 70-680 VCE dumps. Welcome to visit our website — passleader.com — and get the premium 580q 70-680 exam questions.
keywords: 70-680 exam,580q 70-680 exam dumps,580q 70-680 exam questions,70-680 pdf dumps,70-680 vce dumps,70-680 braindumps,70-680 practice tests,70-680 study guide,TS: Windows 7, Configuring Exam
QUESTION 51
You have a computer that runs Windows 7. The computer contains one hard disk. The hard disk is configured as shown in the following table: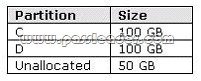
You install a new 250-GB hard disk in the computer. You need to ensure that all the files on the computer are available if a single disk fails. What should you do?
A. Create a mount point on C and D and then create a striped volume.
B. Create a mount point on C and D and then create two striped volumes.
C. Convert both disks to dynamic disks and then create a mirrored volume.
D. Convert both disks to dynamic disks and then create two mirrored volumes.
Explanation:
Creating a Mirrored Volume (RAID-1)A mirrored or RAID-1 volume provides availability and fault tolerance but does not improve performance. It uses two disks (or two portions on separate disks) that are the same size. Any changes made to the first disk of a mirror set are also made to its mirror disk. If the first disk fails, the mirror is broken and the second disk is used until the first is repaired or replaced. The mirror is then re-created, and the information on the working disk is mirrored on the repaired disk. The disadvantage of RAID-1 is that you need (for example) two 200-GB disks to hold 200 GB of data. The advantage is that you can mirror a system disk containing your operating system.You create a mirrored volume using a very similar procedure to the one that creates a striped volume, except that you right-click the first disk of your mirror and click New Mirrored Volume to start the appropriate wizard. You then select the second disk. The second disk needs to have a portion of unallocated space that is at least as large as the disk you want to mirror. The drive letter for a mirrored volume is the same as the drive letter of the first disk. You can also use the Diskpart tool to create a mirrored volume. At the DISKPART> prompt you first use the select disk command to select the first disk. You then enter a command with the syntax add disk=<n>to specify the mirror disk.
QUESTION 52
You have two portable computers that run Windows 7. The computers are not connected to a network. The computers are configured as shown in the following table: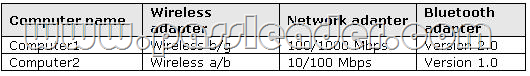
You need to transfer a 1 GB file from Computer1 to Computer2. What should you do first?
A. On Computer1, create a wireless ad hoc network.
B. On Computer2, configure the Bluetooth File Transfer Wizard to send files.
C. On Computer2, create a network profile to connect to a network named Homegroup.
D. On Computer1, configure the computer to be a member of a workgroup named Homegroup.
Answer: A
Explanation:
Wireless Ad Hoc network. You can set up a temporary wireless network, or ad hoc network, between two or more computers running Windows 7 (or between computers running Windows 7 and Windows Vista) provided they are all within 30 feet (9 meters) of each other. A WAP is not required to set up an ad hoc network. This enables users to share folders and other resources without needing to connect to an organizational network. On the first computer on the network, you open Network And Sharing Center and click Set Up A New Connection Or Network. You then choose the option Set Up A Wireless Ad Hoc (Computer To Computer) Network. You give the network a name and (if you want) set up a security key so that users joining the network need to supply a password. For WEP, this can be 5 case-sensitive characters, 13 case-sensitive characters, 10 hexadecimal caseinsensitive characters, or 26 hexadecimal case-insensitive characters, depending on security considerations. (If you choose WPA-2 Personal, you can insist on a 64-character password, but by the time everyone has typed it in correctly, the meeting would probably be over.)BluetoothWindows supports Bluetooth version 1.1 and later versions. Windows does not support Bluetooth version 1.0 because that specification lacks several critical updates that Windows requires to support Bluetooth wireless technology well.
QUESTION 53
You have a computer that runs Windows Vista. The hard disk is configured as shown in the exhibit. (Click the Exhibit button.) You need to install Windows 7 in a dual-boot configuration. What should you do?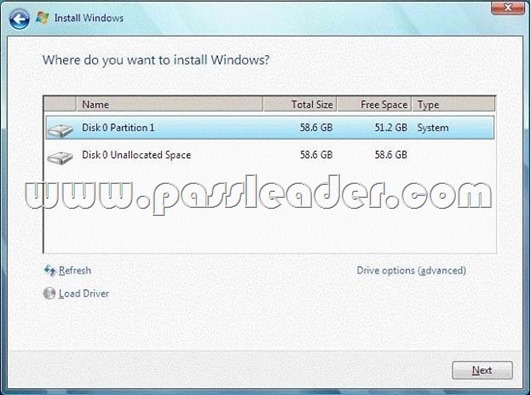
A. From Windows Vista, extend Disk 0 Partition 1.
Install Windows 7 in Disk 0 Partition 1.
B. From Windows Vista, create a new partition.
Install Windows 7 in Disk 0 Partition 1.
C. Start the computer from the Windows 7 installation media.
Install Windows 7 in Disk 0 Partition 1.
D. Start the computer from the Windows 7 installation media.
Install Windows 7 in the unallocated space on Disk 0.
Answer: D
Explanation:
The key to configuring dual-booting is ensuring that each operating system has its own partition or hard disk drive. To dual-boot with Windows 7, you need to be able to create a new volume of at least 15 GB. Even if you have more free space available on the volume you want to shrink, you may not be able to create a volume of the appropriate size because Windows Vista may not be able to move some special types of data to a different place on the hard disk drive. When configuring a new computer to boot between multiple operating systems, it is also necessary to install operating systems in the order that they were released. For example, if you want to boot between Windows XP and Windows 7 on a new computer, you need to install Windows XP before you install Windows 7. If you install Windows XP after Windows 7, the Windows XP installation routine cannot recognize the Windows 7 operating system installation, and the computer only boots into Windows XP. It is possible to repair the computer from this point using Windows 7 startup repair so that it dual-boots, but the simplest course of action is just to install the operating systems in the order in which they were released by Microsoft.
QUESTION 54
You have a computer that runs Windows 7. The computer is in a workgroup. You need to ensure that you can decrypt Encrypting File System (EFS) files on the computer if you forget your password. What are two possible ways to achieve this goal? (Each correct answer presents a complete solution. Choose two.)
A. From Credential Manager, select Back up vault.
B. From User Accounts, select Create a password reset disk.
C. From User Accounts, select Manage your file encryption certificates.
D. From Authorization Manager, modify the Authorization Manager options.
Answer: BC
Explanation:
Password reset disks. It is not unusual for users to forget their passwords to local user accounts from time to time, especially when they use strong passwords. Before the advent of password reset disks, the only way for administrators to restore a forgotten local user account password was to manually reset the user’s password. In the process, the following information was lost: E- mail that was encrypted with the user’s public key Internet passwords that were saved on the computer Files that the user had encrypted Password reset disks offer another solution to the problem of a forgotten password for a local user account. If users create password reset disks for their local accounts before they forget their passwords, they can reset the passwords without losing valuable data that was lost previously with administrative password resets. When you create a password reset disk, a public key and private key pair are created. The private key is stored on a disk: the password reset disk. The public key encrypts the local user account password. If users forget their passwords, they can insert the password reset disk, which contains the private key, and decrypt the current password. The Forgotten Password Wizard prompts the user for a new password, which is then encrypted with the public key. Data is not lost because, basically, the user is simply changing a password. It is essential that password reset disks be stored in secured locations.Back up your Encryption Certificate
1. Open User Accounts by clicking the Start button, clicking Control Panel, clicking User Accounts and Family Safety (or clicking User Accounts, if you are connected to a network domain), and then clicking User Accounts.
2. In the left pane, click Manage your file encryption certificates.
3. In the Encrypting File System wizard, click Next.
4. Click Use this certificate, and then click Next. If you need more details to identify the certificate that is listed, click View certificate. If you want to choose a different certificate, click Select certificate, and then click the certificate you want to back up.
5. Click Back up the certificate and key now.
6. Type or navigate to the location where you want to store the backup. We recommend that you store the backup on removable media such as a disc or USB flash drive.
7. Type and then confirm a password for the backup file, and then click Next. We recommend that you protect the backup file with a strong password.
8. Select the I’ll update my encrypted files later check box, and then click Next.
QUESTION 55
You have a computer that runs Windows 7. You generate a System Diagnostic Report and receive the following warning message:
“The Graphics rating for the system is poor and may be the cause of performance problems.”
You need to increase the graphics performance of the computer without modifying the current hardware or drivers. What should you do?
A. From Personalization, modify the screen saver.
B. From Indexing Options, modify the Advanced options.
C. From Performance Options, modify the visual effects.
D. From Performance Options, modify the processor scheduling.
Answer: C
Explanation:
Configuring Performance Options. The Performance Options tool is a Windows 7 Performance And Analysis tool that you can access by clicking Advanced Tools on the Performance Information And Tools dialog box and then clicking Adjust The Appearance And Performance Of Windows. You can let Windows decide what is best for your computer, adjust for best appearance, adjust for best performance, or select Custom and specify the appearance settings for your computer manually. If you select Custom, you can choose which visual effects to turn off, one by one. There are 18 visual effects that you can control, such as whether shadows are displayed under screen icons or under the mouse pointer. On the Advanced tab, you can adjust for the best performance of programs or background services. If your computer is running applications (as a typical workstation does), you would specify Adjust For Best Performance Of Programs. On a server that is functioning as a Web server (for example), you would specify Adjust For Best Performance Of Background Services.
QUESTION 56
You have two computers named Computer1 and Computer2. Computer1 runs Windows Vista. Computer2 runs Windows 7. You plan to use User State Migration Tool (USMT) 4.0 to migrate user profiles and data from Computer1 to Computer2. You need to prevent some system settings from being migrated. You must achieve this goal by using the minimum amount of administrative effort. Which file should you modify?
A. config.xml
B. migapp.xml
C. migdocs.xml
D. miguser.xml
Answer: A
Explanation:
Config.xml. This file is different from the other migration files as it is used to exclude features from the migration. You can create and modify the Config.xml file using ScanState.exe with the /genconfig option.NOT MigDocs.xmlThis file contains information on the location of user documents.NOT MigUser.xmlMigUser.xml This file contains rules about user profiles and user data. The default settings for this file migrate all data in My Documents, My Video, My Music, My Pictures, desktop files, Start Menu, Quick Launch settings, favorites, Shared Documents, Shared Video, Shared Music, Shared desktop files, Shared Pictures, Shared Start menu, and Shared Favorites. This file also contains rules that ensure that all the following file types are migrated from fixed volumes: .qdf, .qsd, .qel, .qph, .doc, .dot, .rtf, .mcw, .wps, .scd, .wri, .wpd, .xl*, .csv, .iqy, . dqy, .oqy, .rqy, .wk*, .wq1, .slk, .dif, .ppt*, .pps*, .pot*, .sh3, .ch3, .pre, .ppa, .txt, .pst, .one*, .mpp, .vsd, .vl*, .or6, .accdb, .mdb, .pub, .xla, .xlb and .xls. The asterisk ( *) represents zero or more characters.NOT MigApp.xmlThis file contains rules about migrating application settings. These include Accessibility settings, dial-up connections, favorites, folder options, fonts, group membership, Open Database Connectivity (ODBC) settings, Microsoft Office Outlook Express mailbox files, mouse and keyboard settings, phone and modem options, Remote Access Service (RAS) connection phone book files, regional options, remote access, screen-saver settings, taskbar settings, and wallpaper settings.User State Migration ToolUSMT 4.0 is a command-line utility that allows you to automate the process of user profile migration. The USMT is part of the Windows Automated Installation Kit (WAIK) and is a better tool for performing a large number of profile migrations than Windows Easy Transfer. The USMT can write data to a removable USB storage device or a network share but cannot perform a direct side-by-side migration over the network from the source to the destination computer. The USMT does not support user profile migration using the Windows Easy Transfer cable. USMT migration occurs in two phases, exporting profile data from the source computer using ScanState and importing profile data on the destination computer using LoadState.
QUESTION 57
You have a computer that runs Windows 7. You install a second internal hard disk drive in the computer. You attempt to create a system image and discover that the new disk is not listed as a backup destination. You need to ensure that you can use the new disk as a backup destination for system images. What should you do?
A. Create a NTFS partition.
B. Create a mirrored volume.
C. Create a system repair disc.
D. Log on to the computer by using a different account.
Answer: A
Explanation:
If the drive you are saving your backup on is formatted using the NTFS file system and has enough disk space, a System Image of your programs, your operating system, and all drivers and registry settings is also included in the backup.An external hard drive: (Note that the question actually asks about internal) You cannot use an external hard drive for a System Image backup unless you convert its filing system to NTFS. By default external hard drives are formatted using FAT.NOT Accout:The backup account requires administrative privileges to the computer being backed up, but it implys that this was not the issue, since it got to the point were it could see that this disk wasNOT System repair disc:A system repair disc can be used to boot your computer. It also contains Windows system recovery tools that can help you recover Windows from a serious error or restore your computer from a system image. It is not a system image itself.
QUESTION 58
A standard user named User1 has a computer that runs Windows 7. You need to ensure that User1 can run Windows Easy Transfer. What should you do?
A. Disable User Account Control (UAC).
B. Add User1 to the Administrators group.
C. Configure User1 to have a complex password.
D. Copy the support folder from the Windows 7 installation media to the local hard disk drive.
Answer: B
Explanation:
Windows Easy Transfer Migration. After you have set up Windows Easy Transfer on the source computer, you are ready to perform migration. If you want to migrate only a single user account, you can log on with that account to perform the transfer. If you want to migrate all accounts on the computer, you need to log on with a user account that has Local administrator privileges. To do this, start Windows Easy Transfer, select the transfer method, and then, on the Which Computer Are You Using Now? page, select This Is My Old Computer. If you are using the External Hard Disk or USB storage device method, Windows Easy Transfer will then perform a migration check and provide an estimate of the size of the data you can transfer to the new computer on the source computer. If you are using the Network or Easy Transfer Cable method, you will select items for migration on the destination computer.
NOT User Account Control (UAC). UAC is a security feature of Windows 7 that informs you when the action that you want to undertake requires an elevation of privileges. If you logged on with a user account that was a member of the local administrators group in previous versions of Microsoft Windows, such as Windows XP, you automatically had administrator-level access at all times. This, by itself, was not a problem because recommended good practice was that people logged on with accounts that were members of the local administrator group only when they needed to do something related to administration. The problem with this is that people tended to use their administrator account as their normal user account. It was convenient for them because they did not have to log off and log on again each time they wanted to do something related to systems administration. Unfortunately, this behavior presented a security problem because any program run by a user logged on with an administrative account runs with the rights and privileges of that user. UAC resolves this problem by allowing a user that is a member of the local Administrators group to run as a standard user most of the time and to briefly elevate their privileges so that they are running as administrators when they attempt to carry out specific administration-related tasks.
QUESTION 59
You have a computer named Computer1 that runs Windows 7. You plan to migrate the user state on Computer1 by using User State Migration Tool (USMT) 4.0. You need to identify which user documents will be included in the migration. What should you do?
A. Run Usmtutils.exe and use the /ec option.
B. Run Sysprep.exe and use the /audit option.
C. Run Loadstate.exe and use the /v:12 option.
D. Run Scanstate.exe and use the /genmigxml option.
Answer: D
Explanation:
ScanState. You run ScanState on the source computer during the migration. You must run ScanState.exe on computers running Windows Vista and Windows 7 from an administrative command prompt. When running ScanState on a source computer that has Windows XP installed, you need to run it as a user that is a member of the local administrators group. The following command creates an encrypted store named Mystore on the file share named Migration on the file server named Fileserver that uses the encryption key Mykey: scanstate \\fileserver\migration\mystore /i:migapp.xml /i:miguser.xml /o /config:config.xml /encrypt /key:”mykey”/genmigxml: path to a file This option specifies that the ScanState command should use the document finder to create and export an .xml file that defines how to migrate all of the files on the computer on which the ScanState command is running.
QUESTION 60
You are the administrator of a computer named Computer1 that runs Windows 7. Several users share Computer1. The users plan to encrypt files on the computer. You need to ensure that you can access all encrypted files on the computer. What should you do first?
A. At a command prompt, run Cipher.exe.
B. At a command prompt, run Certutil.exe.
C. From the local comput er policy, modify the User Rights Assignment.
D. From User Accounts, run the Manage your file encryption certificates wizard.
Answer: A
Explanation:
Cipher. Displays or alters the encryption of folders and files on NTFS volumes. Used without parameters, cipher displays the encryption state of the current folder and any files it contains. Administrators can use Cipher.exe to encrypt and decrypt data on drives that use the NTFS file system and to view the encryption status of files and folders from a command prompt. The updated version adds another security option. This new option is the ability to overwrite data that you have deleted so that it cannot be recovered and accessed. When you delete files or folders, the data is not initially removed from the hard disk. Instead, the space on the disk that was occupied by the deleted data is “deallocated.” After it is deallocated, the space is available for use when new data is written to the disk. Until the space is overwritten, it is possible to recover the deleted data by using a low-level disk editor or data-recovery software. If you create files in plain text and then encrypt them, Encrypting File System (EFS) makes a backup copy of the file so that, if an error occurs during the encryption process, the data is not lost. After the encryption is complete, the backup copy is deleted. As with other deleted files, the data is not completely removed until it has been overwritten. The new version of the Cipher utility is designed to prevent unauthorized recovery of such data.
/K Creates a new certificate and key for use with EFS. If this option is chosen, all the other options will be ignored. By default, /k creates a certificate and key that conform to current group plicy. If ECC is specified, a self-signed certificate will be created with the supplied key size.
/R Generates an EFS recovery key and certificate, then writes them to a .PFX file (containing certificate and private key) and a .CER file (containing only the certificate). An administrator may add the contents of the .CER to the EFS recovery policy to create the recovery for users, and import the .PFX to recover individual files. If SMARTCARD is specified, then writes the recovery key and certificate to a smart card. A .CER file is generated (containing only the certificate). No .PFX file is genereated. By default, /R creates an 2048-bit RSA recovery key and certificate. If EECC is specified, it must be followed by a key size of 356, 384, or 521.
http://www.passleader.com/70-680.html
QUESTION 61
You have a computer that runs Windows 7. The Encrypting File System (EFS) key is compromised. You need to create a new EFS key. Which command should you run?
A. Certutil -GetKey
B. Cipher.exe /k
C. Lcacls.exe /r
D. Syskey.exe
Answer: B
Explanation:
Cipher. Displays or alters the encryption of folders and files on NTFS volumes. Used without parameters, cipher displays the encryption state of the current folder and any files it contains.Administrators can use Cipher.exe to encrypt and decrypt data on drives that use the NTFS file system and to view the encryption status of files and folders from a command prompt. The updated version adds another security option. This new option is the ability to overwrite data that you have deleted so that it cannot be recovered and accessed.When you delete files or folders, the data is not initially removed from the hard disk. Instead, the space on the disk that was occupied by the deleted data is “deallocated.” After it is deallocated, the space is available for use when new data is written to the disk. Until the space is overwritten, it is possible to recover the deleted data by using a low-level disk editor or data-recovery software.If you create files in plain text and then encrypt them, Encrypting File System (EFS) makes a backup copy of the file so that, if an error occurs during the encryption process, the data is not lost. After the encryption is complete, the backup copy is deleted. As with other deleted files, the data is not completely removed until it has been overwritten. The new version of the Cipher utility is designed to prevent unauthorized recovery of such data.
/K Creates a new certificate and key for use with EFS. If this option is chosen, all the other options will be ignored. By default, /k creates a certificate and key that conform to current group plicy. If ECC is specified, a self-signed certificate will be created with the supplied key size. /R Generates an EFS recovery key and certificate, then writes them to a .PFX file (containing certificate and private key) and a .CER file (containing only the certificate). An administrator may add the contents of the .CER to the EFS recovery policy to create the recovery for users, and import the .PFX to recover individual files. If SMARTCARD is specified, then writes the recovery key and certificate to a smart card. A .CER file is generated (containing only the certificate). No .PFX file is genereated. By default, /R creates an 2048-bit RSA recovery key and certificate. If EECC is specified, it must be followed by a key size of 356, 384, or 521.
QUESTION 62
You have a portable computer that runs Windows 7. The computer is configured to keep an offline version of files located in a network share. You need to identify whether you are working on an offline version of a file. What should you do?
A. From Sync Center, click View sync partnerships.
B. From Action Center, click View archived messages.
C. From Windows Explorer, select the file and then view the toolbar.
D. From Windows Mobile Device Center, click the Connection settings.
Answer: C
Explanation:
To find out whether you’re working offline: Offline files turn on automatically if you lose your network connection. A copy of your file is copied to your computer, and once your network connection is re-established, the two copies will be synchronized. To find out if you’re working offline, do the following.
1. Open the network folder that contains the file you are working on.
2. Check the Details pane at the bottom of the window for the status. If the status is offline, you are working with a copy of the file on your computer. If the status in online, you are working with the file on the network.
QUESTION 63
You have a computer that runs Windows 7. You mark a folder as Always available offline. You need to verify that an offline copy of the folder has been created on the computer. What should you do?
A. Open Sync Center and review the status.
B. Open Action Center and review any messages or issues.
C. Open Windows Mobile Device Center and review the status.
D. Open Network and Sharing Center and review the status for the local area connection.
Answer: A
Explanation:
What is Sync Center?Sync Center allows you to check the results of your recent sync activity if you’ve set up your computer to sync files with a network server. This allows you to access copies of your network files even when your computer isn’t connected to the network. Sync Center can tell you if the files synced successfully or if there are any sync errors or warnings. NoteSync Center is designed to help you sync with files in network locations. If you want to sync a mobile device with your computer, such as a mobile phone or portable music player, Windows gives you several other options. You can install the sync software that some manufacturers include with their device, or you can use the new Device Stage feature in this version of Windows if your device supports this feature. For more information, see Sync music, pictures, contacts, and calendars with a mobile device.
QUESTION 64
Your company has a server that runs Windows Server 2008 R2. The server is configured as a remote access server. The external firewall has TCP port 80 and TCP port 443 open for remote access connections. You have a home computer that runs Windows 7. You need to establish secure remote access connection from the home computer to the remote access server. Which type of connection should you configure?
A. IPSec
B. L2TP
C. PPTP
D. SSTP
Answer: D
Explanation:
Secure Socket Tunneling Protocol. Secure Socket Tunneling Protocol (SSTP) is a new form of VPN tunnel with features that allow traffic to pass through firewalls that block PPTP and L2TP/IPsec traffic. SSTP provides a mechanism to encapsulate PPP traffic over the SSL channel of the HTTPS protocol. The use of PPP allows support for strong authentication methods such as EAP- TLS. The use of HTTPS means traffic will flow through TCP port 443, a port commonly used for Web access. Secure Sockets Layer (SSL) provides transport-level security with enhanced key negotiation, encryption, and integrity checking.
QUESTION 65
You have a computer that runs Windows 7. You need to record when an incoming connection is allowed through Windows firewall. What should you do?
A. In Local Group Policy, modify the audit policy.
B. In Local Group Policy, modify the system audit policy.
C. From the Windows Firewall with Advanced Security properties, set the logging settings to Log successful connections.
D. From the Windows Firewall with Advanced Security properties, set the Data Protection (Quick Mode) IPSec settings to Advanced.
Answer: C
Explanation:
Customize Logging Settings for a Firewall Profile. Windows Firewall with Advanced Security can be configured to log events that indicate the successes and failures of its processes. The logging settings involve two groups of settings: settings for the log file itself and settings that determine which events the file will record. The settings can be configured separately for each of the firewall profiles. You can specify where the log file will be created, how big the file can grow, and whether you want the log file to record information about dropped packets, successful connections, or both. Log successful connectionsUse this option to log when Windows Firewall with Advanced Security allows an inbound connection. The log records why and when the connection was formed. Look for entries with the word ALLOW in the action column of the log.
QUESTION 66
Your company has a server named Server1 that runs Windows Server 2008. Server1 is a Windows Server Update Services (WSUS) server. You have a computer named Computer1 that runs Windows 7. Computer1 is configured to obtain updates from Server1. You open the WSUS snap-in on Server1 and discover that Computer1 does not appear. You need to ensure that Computer1 appears in the WSUS snap-in. What should you do?
A. On Server1, open Windows Update then select Check for updates.
B. On Server1, run Wsusutil.exe and specify the /import parameter.
C. On Computer1, open Windows Update and then select Change settings.
D. On Computer1, run Wuauclt.exe and specify the /detectnow parameter.
Answer: D
Explanation:
wuauclt.exeThe wuauclt utility allows you some control over the functioning of the Windows Update Agent. It is updated as part of Windows Update.Detectnow OptionBecause waiting for detection to start can be a time-consuming process, an option has been added to allow you to initiate detection right away. On one of the computers with the new Automatic
Update client installed, run the following command at the command prompt:
wuauclt.exe /detectnow
QUESTION 67
You have a computer that runs Windows 7. Windows Update settings are configured as shown in the exhibit. (Click the Exhibit button.) You discover that standard users are never notified when updates are available. You need to ensure that standard users are notified when updates are available. What should you do?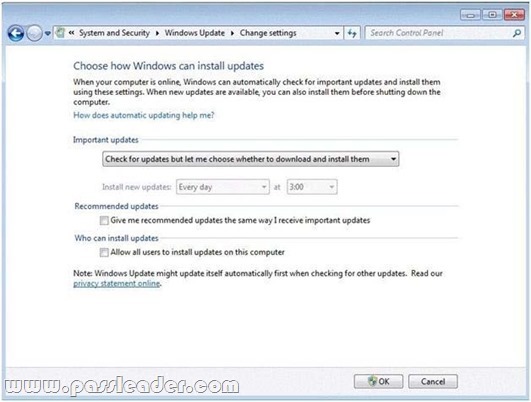
A. Select Allow all users to install updates on this computer.
B. Specify an intranet Microsoft update service location in Group Policy.
C. Change the Startup Type for the Windows Update service to Automatic.
D. Select Give me recommended updates the same way I receive important updates.
Answer: A
Explanation:
Change how Windows installs or notifies you about updates You can set Windows to automatically install important and recommended updates or to install important updates only. Important updates provide significant benefits, such as improved security and reliability. Recommended updates can address noncritical problems and help enhance your computing experience. Optional updates are not downloaded or installed automatically. If you don’t want updates to be installed automatically, you can choose to be notified when updates apply to your computer instead. Then, you can download and install them yourself, or you can set Windows to automatically download updates, and then notify you so you can install them yourself. Here’s how to change how Windows installs or notifies you about updates:
1. Click to open Windows Update.
2. In the left pane, click Change settings.
3. Under Important updates, click one of the following:
4. To schedule your automatic updates, next to Install new updates, select the day and time you want updates to occur. – Install updates automatically (recommended)
– Download updates but let me choose whether to install them
– Check for updates but let me choose whether to download and install them
– Never check for updates (not recommended)
5. To get recommended updates for your computer, under Recommended updates, select the Give me recommended updates the same way I receive important updates check box.
6. To allow anyone using the computer to make updates, select the Allow all users to install updates on this computer check box. This applies only to updates and software that are installed manually; automatic updates will be installed regardless of the user.
7. Click OK. If you’re prompted for an administrator password or confirmation, type the password or provide confirmation.
QUESTION 68
You have a computer that runs Windows 7. Your computer’s disk configuration is shown in the exhibit. (Click the Exhibit button.) You need to ensure that you can create a striped volume on the computer. What should you do?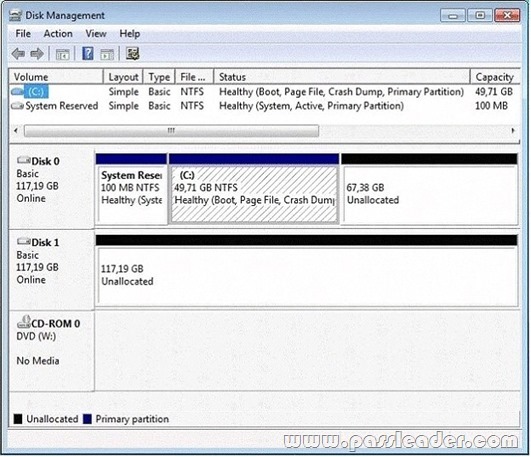
A. Add an additional hard disk.
B. Convert all disks to dynamic disks.
C. Install a digitally-signed disk driver.
D. Set the Startup Type of the Virtual Disk Service (VDS) to Automatic.
Answer: B
Explanation:
A striped volume is a dynamic volume that stores data in stripes on two or more physical disks. Data in a striped volume is allocated alternately and evenly (in stripes) across the disks. Striped volumes offer the best performance of all the volumes that are available in Windows, but they do not provide fault tolerance. If a disk in a striped volume fails, the data in the entire volume is lost. You can create striped volumes only on dynamic disks. Striped volumes cannot be extended. You can create a striped volume onto a maximum of 32 dynamic disks. Backup Operator or Administrator is the minimum membership required to complete the actions below.
Creating a striped volume
Using the Windows interface
Using a command line
To create a striped volume using the Windows interface In Disk Management, right-click the unallocated space on one of the dynamic disks where you want to create the striped volume, and then click New Striped Volume…
Follow the instructions on your screen.
To create a striped volume using a command line
Open a command prompt and type diskpart.
At the DISKPART prompt, type list disk. Make note of the number of the disk where you want to create a striped volume.
At the DISKPART prompt, type create volume stripe [size=<size>] [disk=<disknumber>[,[<seconddisknumber>, …]].
QUESTION 69
You have a computer that runs Windows 7. The computer is configured to automatically download and install updates. You install Microsoft Office 2007. You need to ensure that service packs for Office are automatically installed. What should you do?
A. From Windows Update, select Restore hidden updates.
B. From Windows Update, select Get updates for other Microsoft products.
C. Create a folder named Updates in C:\Program Files\Microsoft Office. Install the Office Update Inventory Tool into the Updates folder.
D. Download and install the Office 2007 administrative template and disable the Block updates from the Office Update Site from applying policy.
Answer: B
Explanation:
Use Windows Update to Check for Updates to other Microsoft Products By default, Windows Update can download and install updates for Windows 7 and features that are part of the operating system (such as Internet Explorer). You can also merge the functionality of Microsoft Update–a service for managing updates to Microsoft Office and several other Microsoft products–into Windows Update so that you no longer need to visit Office Online to get updates.If you do not already have Windows Update integrated with Microsoft Update, you will see the message “Get updates for other Microsoft products” on the Windows Update home page. To enable checking for other products, click the Find Out More option shown beside this message. This will take you to the Microsoft Update site for some quick installation steps. You only need to do this once. Thereafter, the Windows Update home page will indicate that you receive updates “For Windows and other products from Microsoft Update.”
QUESTION 70
You need to uninstall a Windows update from a computer that runs Windows 7. Which Control Panel item should you use?
A. Administrative Tools
B. Programs and Features
C. Sync Center
D. Troubleshooting
Answer: B
